A surge in “… will damage your computer” pop-ups is driving Mac users nuts
macOS Big Sur and Catalina are massively alerting users to malware on their computers by recurrently displaying “… will damage your computer” pop-up dialogs.
In cybersecurity, the line between a real heads-up and a false positive is blurred. Sometimes the latter is an upshot of over-protection on a service provider’s end, and it can as well be a shortcoming of malware detection algorithms. One way or another, the user is on the receiving end of incessant warnings that make the computing experience go down the drain.
In recent havoc that broke out in the Mac territory, numerous users found themselves in a situation where their machines keep displaying alerts that say, “[App Name] will damage your computer. You should move it to the Trash”. The fact that these pop-ups come in insanely large numbers makes some users think that this is a macOS bug. However, that’s a misconception – and here is why.
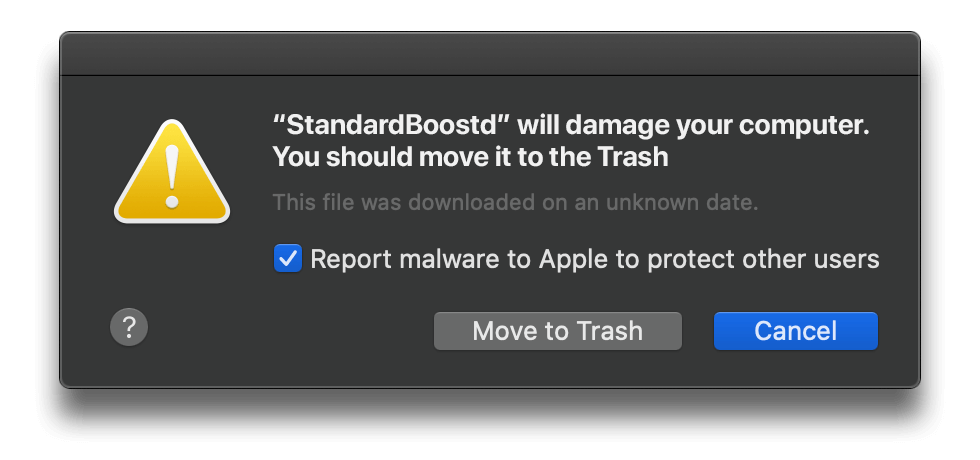
The incredibly annoying “… will damage your computer” alerts are triggered because macOS has started ringing the alarm bells in response to real malware activity on specific computers in late February 2021. Notice the vanilla-looking application name in quotes (StandardBoostd) on the screenshot above. This is one of the multiple strains of malicious code invoking an abnormally aggressive reaction of the operating system. Some of the other common samples mentioned in these pop-ups warnings at this point are as follows:
- ConfigTyped
- DominantPartitiond
- ElementaryTyped
- ManagerAnalogd
- OperativeMachined
- ProtocolStatus
- TrustedAnalogd
This is far from being a complete list of unwanted apps that have ended up in the spotlight of macOS Gatekeeper, a feature that checks code for notarization issues and known signs of malicious behavior. What most of them have in common is the affiliation with an adware family called AdLoad, which cashes in on freeware bundles to infect Macs on a large scale.
The most rational theory about what’s happening is that Apple’s protection mechanisms have been recently improved, and AdLoad spin-offs along with a few other adware lineages are now easily detectable. These enhancements may have arrived with macOS Big Sur and macOS Catalina feature updates, or the Cupertino company could have quietly rolled out a series of tweaks to Gatekeeper logic beyond the regular update schedule.
That’s good news for the Mac user community, but with the caveat that the “… will damage your computer” alerts are splashing up non-stop without providing any effective methods to apply a permanent fix. Although most of these dialogs include a “Move to Trash” button, it doesn’t do what it says. As a result, users are stuck between a rock and a hard place. On the one hand, they are bombarded by nuisance pop-ups from macOS. On the other, they are faced with stubborn adware that resists commonplace removal.
It appears that the only workaround is to go the extra mile checking a handful of folders for sketchy files and deleting them, or outsourcing this tedious work to a trusted Mac antimalware tool. Hopefully, Apple will be combining its threat detection refinements with hands-on cleaning methods further down to minimize users’ frustration when outbreaks like this occur.