Beware of New Android Ransomware Called DoubleLocker
DoubleLocker is the first Android ransomware that utilizes the Accessibility Service. Malware may encrypt user data; it can also lock the device.
DoubleLocker is built on the basis of a famous bank Trojan called Svpeng. DoubleLocker uses Svpeng’s code parts to encrypt and lock files but cannot collect user’s bank data and delete accounts.
DoubleLocker can change the device PIN and block the access for the victim. It also encrypts all data. This combination of Android malware features is seen for the first time.
 Given the origin of the Svpeng bank malware, DoubleLocker could be turned into what we call ransomware. The malware acts in two stages – it tries to delete the bank or PayPal account and then blocks the data and device to demand a ransom. We found a test version of this ransomware in May 2017.
Given the origin of the Svpeng bank malware, DoubleLocker could be turned into what we call ransomware. The malware acts in two stages – it tries to delete the bank or PayPal account and then blocks the data and device to demand a ransom. We found a test version of this ransomware in May 2017.
DoubleLocker is distributed in a very simple way. Like its ancestor the Svpeng banking Trojan, it pretends to be an Adobe Flash Player being pushed on hacked websites.
Once activated, the malware suggests allowing a special feature called Google Play Service. Having received the necessary permissions, the malware uses them to put its hands on administrator rights and becomes the sole launcher app – all without the user’s approval.
Self-promotion as a default launcher increases the persistence of the malware. When the person pushes the Home button, the ransomware is being re-activated and the device gets locked again.
Once launched on the device, DoubleLocker uses several strong arguments to force the user to pay the ransom.
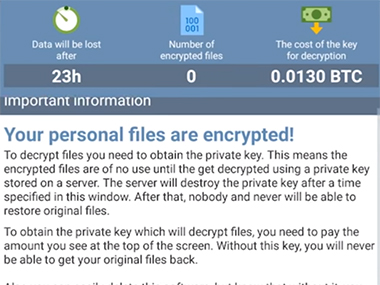
First of all, DoubleLocker changes the device PIN and prevents the user to operate it. A new PIN is selected from a random value. The PIN is not going to be stored on the device. Crooks do send anywhere outside either. So the victim and security professionals cannot recover it. But after receiving the payment, an attacker can remotely reset the PIN and unlock the device.
Secondly, DoubleLocker encrypts all files located on the device’s primary storage. It makes use of the strong AES encryption algorithm and adds the strange .cryeye file extension.
The ransom amount is 0.0130 Bitcoins. The ransom note emphasizes that victims should send the payment within 24 hours. If they fail to do so, the data will remain encrypted forever.
The sole way to remove the DoubleLocker is to reset the device to the factory settings. Encrypted files cannot be restored.
For prevention, we recommend that you protect your Android-based devices with high-quality security products and make backups on a regular basis.

Add A Comment