GandCrab v3 ransomware released: not really a game-changer
With ransomware in general plummeting so far in 2018, GandCrab is one of the few strains that stay afloat and keep evolving. This infection was apparently coined by skilled cybercrooks as it exhibits a rock-sold crypto functionality, clever distribution and enviable durability in the face of the law enforcement’s efforts to counter the plague. Although it has gone through C2 server takedown by the police earlier this year, it revived with yet more vicious, well-orchestrated attacks.
Security researchers spotted a brand new variant of this ransomware in early May. It has reached version 3, and the changes aren’t isolated to the number alone. GandCrab v3 goes equipped with a desktop wallpaper replacement feature similar to how the nasty Locky and Cerber used to instill fear to its victims. The way it handles hostage files, though, remains unaltered – each one is still appended with the .CRAB extension. The ransom note continues to be a document named CRAB-DECRYPT.txt.
 The overhauled culprit boasts multi-vector propagation. One of the payload delivery techniques comes down to malspam, where would-be preys receive emails masqueraded as customer support notifications from a bank. These phishing emails contain a ZIP archive attachment that, when unpacked, fires up a VBS downloader behind the scenes. This entity is the one liable for installing GandCrab v3 onto a target host. Another mechanism of infection is based on the Magnitude exploit kit. In this case, all it takes to get contaminated is visit a hacked website with toxic scripts surreptitiously running on it.
The overhauled culprit boasts multi-vector propagation. One of the payload delivery techniques comes down to malspam, where would-be preys receive emails masqueraded as customer support notifications from a bank. These phishing emails contain a ZIP archive attachment that, when unpacked, fires up a VBS downloader behind the scenes. This entity is the one liable for installing GandCrab v3 onto a target host. Another mechanism of infection is based on the Magnitude exploit kit. In this case, all it takes to get contaminated is visit a hacked website with toxic scripts surreptitiously running on it.
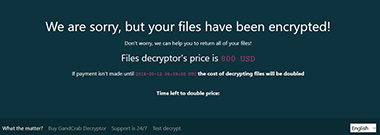
The above-mentioned desktop background can be sort of an issue to the attackers. Due to a bug in this routine, the ransomware may lock the user’s screen altogether instead of simply displaying the alert. This may prevent victims from even getting to the point where they learn the ransom demands and possibly decide to pay up. By the way, the extortionists instruct those infected to visit a dedicated payment page via Tor Browser. The size of the ransom indicated on that page is 800 USD, and it’s payable in Dash or Bitcoin cryptocurrency.
Overall, this update of the notorious GandCrab pest has introduced hardly anything revolutionary. However, it is still an extremely dangerous blackmail malware that cannot be decrypted without submitting the ransom.